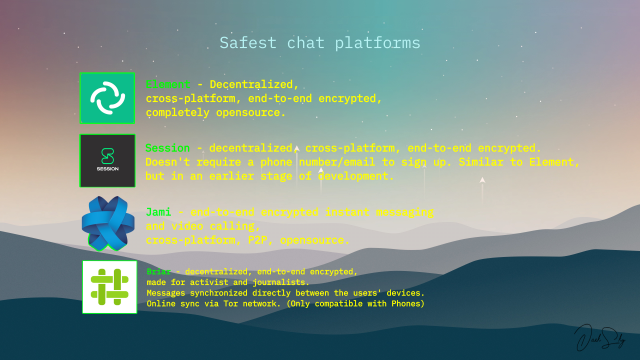
Lots of people are looking for secure chat platforms and stuff like that. So I thought I'd create a poster.
I excluded Telegram because it's pretty much like WhatsApp. And this https://iddqd.press/2019/12/11/telegram-is-an-obvious-honeypot.html
I would've included Signal, but I'm being skeptical here and Signal looks a bit suspicious since it requires your phone number etc.
What are your thoughts on this?
#tech
#technology
#security
#privacy
I excluded Telegram because it's pretty much like WhatsApp. And this https://iddqd.press/2019/12/11/telegram-is-an-obvious-honeypot.html
I would've included Signal, but I'm being skeptical here and Signal looks a bit suspicious since it requires your phone number etc.
What are your thoughts on this?
#tech
#technology
#security
#privacy
Telegram Is An Obvious Honeypot
I've seen a rash of rightists on the Internet bring up Telegram as some kind of "secure" alternative to Discord and Twitter, bringing up how it has "end-to-end encryption" or whatever else.IDDQD Press
Gilbert Busana
in reply to Gilbert Busana • • •Not sure about Session here. They have a cryptocurrency token tie-in that somehow is supposed to make the network "safer" (than Tor), but some small amount of mined tokens is hard-coded to always go to the organization behind Session:
https://mastodon.social/@rysiek/106542118359065380
🤔
Rysiekúr (old account) (@rysiek@mastodon.social)
MastodonGilbert Busana
in reply to Gilbert Busana • • •1. Telegram is very open that they are not end-to-end encrypted by default and never portray themselves as anything else. Secret chats are e2e and nothing more.
1. Cloud chats are encrypted in transit and in storage. Encryption keys are broken up into pieces and stored in various jurisdictions, making it virtually impossible to legally force giving up data to governments.
1. Whatsapp is never secure. As there have been countless exploits in it where you can gain full access to the remote device. No such exploit, or really any, has ever existed in Telegram.
1. TG accepts 3rd party clients to it's open API.
1. TG let's you validate that the mobile client you install on your phone is the same as the source code published in their public repos
1. The backend is closed source but I always thought that was a dumb thing to mention because you have no idea what's actually running on the servers in the end.
1. Signal has suspect funding (read Surveillance Valley)
1. Signal does not allow 3rd party clients to use it's op... show more
1. Telegram is very open that they are not end-to-end encrypted by default and never portray themselves as anything else. Secret chats are e2e and nothing more.
1. Cloud chats are encrypted in transit and in storage. Encryption keys are broken up into pieces and stored in various jurisdictions, making it virtually impossible to legally force giving up data to governments.
1. Whatsapp is never secure. As there have been countless exploits in it where you can gain full access to the remote device. No such exploit, or really any, has ever existed in Telegram.
1. TG accepts 3rd party clients to it's open API.
1. TG let's you validate that the mobile client you install on your phone is the same as the source code published in their public repos
1. The backend is closed source but I always thought that was a dumb thing to mention because you have no idea what's actually running on the servers in the end.
1. Signal has suspect funding (read Surveillance Valley)
1. Signal does not allow 3rd party clients to use it's open API (suspect!) and also no way to verify your clients
1. Afaik, no government has ever been successful in forcing TG to give up any data.
1. There is a still unclaimed 6 figure bounty for anyone that can break their encryption (for years now)
1. Finally (I could go all day) I think they are the most open about whatever is going on. That comes off as genuine to me.
Yes, obviously I do like to use Telegram but I wouldn't use it, or any similar service, to send anything that was truly sensitive. Also, does appear to collect more metadata than I'd like but it's still fairly minimal.
Just my $0.02
Gilbert Busana
in reply to Gilbert Busana • • •And I have seen this happen.
There is no good reason to do that.
I think The Grugq put it best:
https://medium.com/@thegrugq/operational-telegram-cbbaadb9013a
Operational Telegram - thaddeus t. grugq - Medium
thaddeus t. grugq (Medium)Gilbert Busana
in reply to Gilbert Busana • • •Gilbert Busana
in reply to Gilbert Busana • • •Making such claims in the context of groups not being end-to-end encrypted at all, and private chats not e2e encrypted by default, is actively harmful.
And sure, they can say "well, on page 20 of our FAQ you can read that you need to enable encrypted private chats". Doesn't fix it.
Gilbert Busana
in reply to Gilbert Busana • • •> Telegram keeps your messages safe from hacker attacks.
...also from their website. In e2e encrypted systems there are no messages that system operators need to "keep safe from hacker attacks". And that's how IM systems should work in AD 2022.
If Telegram team really cared about people's privacy they would deploy e2ee by default as soon as possible, and in the meantime have *super-clear* messaging about the current shortfalls. They don't.
Gilbert Busana
in reply to Gilbert Busana • • •They are clearly not 100% honest with their users about e2ee, why should we trust them on anything else?
Gilbert Busana
in reply to Gilbert Busana • • •Remember TG started a years before Signal existed and before WA added e2ee to it's messaging. Also they're target user isn't security minded hackers/info sec, etc.
I think they're pretty honest about how the tool works. The homepage messaging is definitely marketing dribble but not inaccurate and I don't think anyone but a small subset of people (like you and I) would read that and think "Ah ok, so everything is e2ee by default".
There's nothing in the homepage messaging that to me means "They are clearly not 100% honest with their users about e2ee" - I think that's you reading it through your specific lens.
I also don't think it means they don't care about user privacy. I think they've overwhelmingly shown the opposite to be true.
Like I said before, I wouldn't use TG (or Signal, or <whatever>) to send truly sensitive information ever. I do still think TG is the best daily driver messaging platform and apps that is mostly open about all things and that my messages (as menial as they may be) are protected.
In the en... show more
Remember TG started a years before Signal existed and before WA added e2ee to it's messaging. Also they're target user isn't security minded hackers/info sec, etc.
I think they're pretty honest about how the tool works. The homepage messaging is definitely marketing dribble but not inaccurate and I don't think anyone but a small subset of people (like you and I) would read that and think "Ah ok, so everything is e2ee by default".
There's nothing in the homepage messaging that to me means "They are clearly not 100% honest with their users about e2ee" - I think that's you reading it through your specific lens.
I also don't think it means they don't care about user privacy. I think they've overwhelmingly shown the opposite to be true.
Like I said before, I wouldn't use TG (or Signal, or <whatever>) to send truly sensitive information ever. I do still think TG is the best daily driver messaging platform and apps that is mostly open about all things and that my messages (as menial as they may be) are protected.
In the end, regardless which of these services we use, there's a level of trust that has to be given by the end users.
Gilbert Busana
in reply to Gilbert Busana • • •Gilbert Busana
in reply to Gilbert Busana • • •I've set-up and run five XMPP servers. I've been a pretty heavy XMPP user, and used both OpenPGP and OTR encryption on XMPP.
XMPP is unusable for most people, because the matrix of which client/server software implements which XEPs is a kilometer deep and a mile long.
This means I cannot reliably know if the person I will be talking to will have the particular combination of XEPs available.
Gilbert Busana
in reply to Gilbert Busana • • •> This means I cannot reliably know if the person I will be talking to will have the particular combination of XEPs available.
Wait what? Why would you need to know? It doesn't matter what XEPs their client or server support, you can still easily communicate with them. That's the entire point of the "eXtensible" in the name.
I've had everyone I know on XMPP since 2013ish and have never once had to know or care about what XEPs their software supported.
Gilbert Busana
in reply to Gilbert Busana • • •The point is: certain XEPs have become important enough that "who knows if the other side implements it" is not an acceptable approach. You end up with a lowest-common-denominator thing.
Gilbert Busana
in reply to Gilbert Busana • • •Gilbert Busana
in reply to Gilbert Busana • • •https://en.wikipedia.org/wiki/Comparison_of_XMPP_server_software#Comparison_by_XEP_implementation_status
https://en.wikipedia.org/wiki/Comparison_of_XMPP_clients#IM_Compliance_Suite
Wikimedia list article
Contributors to Wikimedia projects (Wikimedia Foundation, Inc.)Gilbert Busana
in reply to Gilbert Busana • • •You said differing XEP support made XMPP unusable, I said it absolutely did not and doesn't matter. You brought up OMEMO which requires all clients to clearly indicate support, and are now linking lists of XEPs, which again, don't matter...
Gilbert Busana
in reply to Gilbert Busana • • •My point was broader and it was about the incompatibilities between different combinations of XMPP clients and servers stemming from spotty implementation of XEPs in said clients and servers. And about the usability challenges that stem from that.
This whole branch of the thread is a pretty good example of proponents of XMPP not accepting criticism, instead of fixing things.
Gilbert Busana
in reply to Gilbert Busana • • •*Most* everyone runs a modern well supported client, like Conversations, Dino, Siskin, Gajim to name a few, but even if your contact wants the pain of running pidgin that doesn't affect you.
XMPP's only problem is combatting decades of misinformation from people that connected to gtalk using pidgin once in 2006 and found it to be a bad experience (it was terrible!), but it's been the best IM experience for well over a decade at this point, and the only one that is a standard with wide adoption and multiple independent implementations that you can run yourself.
Gilbert Busana
in reply to Gilbert Busana • • •We can run in circles for days.
Wake me up when XMPP creates some kind of a *standard* suite of XEPs that *have to* be implemented in clients and/or servers, and some form of "certification" process, so that when I see that a client is (say) "XMPP 2022"-compatible, I know what to expect.
Instead of me having to consult said tables of XEP doom.
Elena ``of Valhalla''
in reply to Gilbert Busana • • •I think that the standard suite of XEPs is in https://xmpp.org/extensions/xep-0459.html and there is a server compliance suite for those at https://compliance.conversations.im/ which publishes the results.
I have a vague memory of a similar test suite for clients, but I can't find anything, so maybe I'm remembering it wrong.
Anyway, most people are using one of the clients with good support, these days, unless they have very specific requirements, so things aren't as bad as they were in the gtalk era.
Roberto Resoli reshared this.