Search
Items tagged with: Cybersecurity
https://gergelykalman.com/no-CVE-batsignal-a-macos-lpe.html #infosec #cybersecurity #security #apple #macos #vulnerability

batsignal (no CVE) - a macOS LPE
UPDATE: A couple hours after publication the Apple Security Changelogs were updated across the board, and they added me to CVE-2022-26704. I knew this was in the works, but it's still good to see.Gergely's hack blog
@hack_lu @libreoffice
#opensource #cybersecurity
If you want also @fsfe and @libreoffice stickers come to see us tomorrow.
#opensource #cybersecurity #hacklu #luxembourg
*do not label your cat.
#News #TechNews #Zoom #China #privacy #cybersecurity #surveillance
https://youtu.be/nxYi26_qTOM
I #computer #quantistici potrebbero presto affrontare problemi che ostacolano i potenti #supercomputer di oggi, anche se pieni di errori.
Calcolo e precisione vanno di pari passo. Ma una nuova collaborazione tra #IBM e UC #Berkeley ha dimostrato che la perfezione non è necessariamente richiesta per risolvere problemi impegnativi, dalla comprensione del comportamento dei materiali #magnetici alla #modellazione del comportamento delle #reti #neurali o della diffusione delle #informazioni sui #socialnetwork.
#redhotcyber #informationsecurity #ethicalhacking #dataprotection #hacking #cybersecurity #cybercrime #cybersecuritytraining #cybersecuritynews #privacy #infosecurity #online
https://www.redhotcyber.com/post/ibm-e-uc-berkeley-dimostrano-che-limperfezione-dei-computer-quantistici-puo-portare-a-risultati-sorprendenti/

IBM e UC Berkeley dimostrano che l'imperfezione dei computer quantistici può portare a risultati sorprendenti
Scopri come i computer quantistici di IBM e UC Berkeley sfidano i potenti supercomputer nell'affrontare problemi complessi. Nonostante gli errori, i risultati sono sorprendentemente accurati.Redazione RHC (Red Hot Cyber)
My team is hiring a Senior Technical Architect to manage the security of the *entire* .gov.uk domain name space.
https://www.civilservicejobs.service.gov.uk/csr/jobs.cgi?jcode=1858768
Happy to chat informally about the role. Big challenges at the heart of Government and a chance to write national level policy.
Fair warning, it is *always* DNS!
#Fedihired

Senior Technical Architect - Civil Service Jobs - GOV.UK
Search and apply for jobs in the UK Civil Servicewww.civilservicejobs.service.gov.uk
https://techcrunch.com/2023/06/01/kaspersky-says-attackers-hacked-staff-iphones-with-unknown-malware/
#cybersecurity #malware #ios
Adrian #Lamo è stato un hacker che ha trovato nuovi modi per violare le aziende e fargli comprendere quanto erano insicure.
Dai primi hack fino ad arrivare ad attacchi informatici verso aziende di prestigio mentre vagabondava con il suo zaino fino all'essere chiamato "spia" dalla comunità degli hacker, Adrian è stato una figura controversa nel mondo dell'hacking ma altamente interessante.
#redhotcyber #informationsecurity #ethicalhacking #dataprotection #hacking #cybersecurity #cybercrime #cybersecurityawareness #cybersecuritytraining #cybersecuritynews #privacy #infosecurity
https://www.redhotcyber.com/post/hacker-famosi-la-storia-di-andrian-lamo

Hacker famosi: la storia di Andrian Lamo
Adrian Lamo è stato un hacker che ha trovato nuovi modi per violare le aziende e fargli comprendere quanto erano insicure.Redazione RHC (Red Hot Cyber)
TL;DR: Don't turn it on.
The new update allows users to sign in with their Google Account and sync 2FA secrets across their iOS and Android devices.
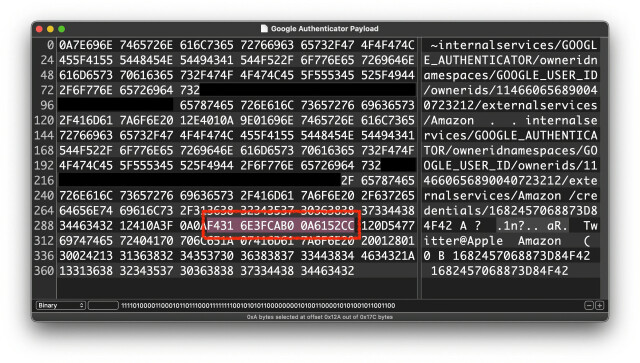
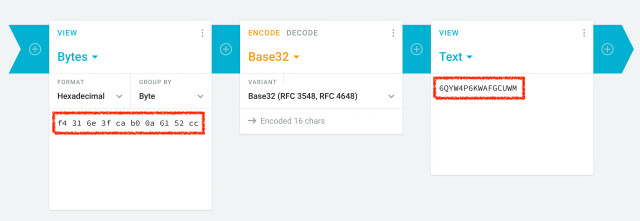
We analyzed the network traffic when the app syncs the secrets, and it turns out the traffic is not end-to-end encrypted. As shown in the screenshots, this means that Google can see the secrets, likely even while they’re stored on their servers. There is no option to add a passphrase to protect the secrets, to make them accessible only by the user.
Why is this bad?
Every 2FA QR code contains a secret, or a seed, that’s used to generate the one-time codes. If someone else knows the secret, they can generate the same one-time codes and defeat 2FA protections. So, if there’s ever a data breach or if someone obtains access .... 🧵
#Privacy #Cybersecurity #InfoSec #2FA #Google #Security